In the modern practice context, the careful handling of sensitive client data in the mental health field is more important than ever. The ‘threat landscape’ of risks to the security of client info continues to rapidly evolve, and the consequences in terms of potential client harm if those threats are realized are also increasingly significant and impactful. How, then, can you best protect the information your clients have entrusted you with?
How security is part of client care
Let’s begin this consideration with some *essential* framing: securing client info is an integral aspect of client care. It is one of the ways in which you hold safe space for your clients. It provides one of the building blocks for establishing an effective therapeutic alliance – and failing to secure client information can cause harm to not only the client outside of therapy, but also to the therapeutic alliance.
This reality is one of the reasons that each of the mental health professions ethics codes explicitly require the safeguarding of the confidentiality of client info. While each of the ethics codes contain this basic requirement, they provide varying degrees of specificity in terms of what this safeguarding actually entails in-practice.
Confidence around ethical responsibilities
How can you know with confidence that you as a provider have done your utmost to uphold your ethical responsibilities to your clients in terms of safeguarding their information?
The answer: HIPAA Security compliance! Yes, really. HIPAA, the Health Insurance Portability and Accountability Act, is a set of regulations designed to protect patients’ sensitive information, and the Office of Civil Rights (OCR) oversees its implementation. HIPAA provides a set of specific Standards and Rules that are an extremely useful [though not perfect] framework and mechanism for securing client info, and thereby also in upholding your ethical responsibilities to your clients.
Time to rethink how we think about HIPAA
It’s time for a paradigm shift in how we view HIPAA: HIPAA is a supportive tool.
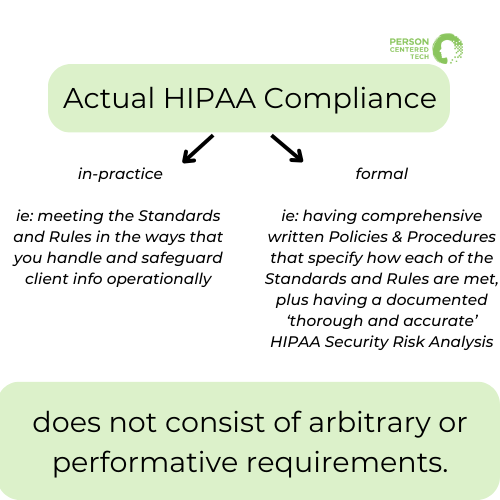
HIPAA compliance is a means to the end of caring for clients through safeguarding the information they’ve entrusted you with, to fulfilling your ethical responsibilities, and to optimizing and fortifying your practice. Actual compliance – in-practice (meeting the Standards and Rules in the ways that you handle and safeguard client info operationally) *and* ‘formal’ (having comprehensive written Policies & Procedures that specify how each of the Standards and Rules are met, plus having a documented ‘thorough and accurate’ HIPAA Security Risk Analysis) – does not consist of arbitrary or performative requirements.

Risk Analysis and HIPAA security compliance
In that context, let’s explore why risk analysis is a fundamental and foundational requirement of HIPAA Security compliance, informed by insights from the OCR’s recent presentation on the risk analysis requirement, and how it plays a crucial role in safeguarding client information for mental health professionals.
- The Basics of HIPAA Security Rule:
The HIPAA Security Rule mandates that all HIPAA covered entities, including mental health professionals, safeguard the confidentiality, availability, and integrity of all protected health information (PHI) they create, receive, maintain, or transmit. PHI is found in various places [systems, devices, physical spaces, etc.,] within a mental health practice, and it is crucial to protect it.
Without a thorough risk analysis, it becomes tremendously challenging to identify potential vulnerabilities and threats, assess the impact of those risks being realized, and evaluate whether reasonable and appropriate safeguards have been implemented which address vulnerabilities and thereby sufficiently reduce the ‘surface area of risk exposure.’ In other words, without a risk analysis you’re not able to properly safeguard your clients’ information… it’s being left to chance and luck.
[In therapy terms: think of the risk analysis as a needs assessment, and the risk mitigation plan as the treatment plan.]
It is for this reason that conducting and documenting a ‘thorough and accurate’ risk analysis and then generating and implementing a risk mitigation plan are foundational requirements for *all* HIPAA covered entities.
- Common Compliance Challenges in the Mental Health Space:
Compliance with the HIPAA Security Rule remains a significant challenge in the mental health space, both for solo practitioners and group practices. Risk Analysis is often the least complied-with requirement of the HIPAA Security Rule in the mental health care provider space. Many practices tend to overlook or underestimate the significance and tangible value of risk analysis.
Furthermore, having the expertise and support to perform a meaningful risk analysis and generate an actionable risk mitigation plan that fits the specific context and needs of a mental health private practice has often felt elusive and been a barrier to compliance with the requirement.
[Awareness of this challenge and need is one of the primary factors that lead PCT to create the solution of our HIPAA Security Risk Analysis & Risk Mitigation Planning service which consists of both a risk analysis tool developed *specifically* for the mental health practice context, and to our providing risk analysis and risk mitigation planning as a supportive, consultant-performed service.]
Key Takeaways from the OCR’s Recent Webinar:
The OCR emphasized the importance of risk analysis and highlighted key points related to HIPAA Security Rule requirements. Some of the key takeaways from the OCR include:
- Understanding the Flow of PHI: It is essential to understand how PHI enters, flows through, and leaves the organization/practice. This involves considering how PHI is received, stored, and transmitted.
Mental health practices receive PHI from clients, other providers, and maintain it in electronic health records (EHR), email systems, and other platforms. PHI is also sent out of the organization, to clients, other care providers, insurance companies, etc., Analyzing the lifecycle of PHI is crucial for safeguarding it effectively. Risk analysis needs to account for how and where information is received, where it lives within your practice, and to whom and how it is released, in order for it to be comprehensive and sufficient.
- Asset and PHI Inventory Mapping: A compliant risk analysis must include an inventory of assets [systems, devices, physical spaces, workforce members, etc.,] that hold or touch PHI, and what kind of PHI each asset contains or has access to. This helps to accurately assess the severity of impact if a threat or vulnerability is realized and evaluate reasonable and appropriate safeguards to protect all PHI.
- Periodicity of Risk Analysis: While there’s no official requirement for the frequency that a formal and documented risk analysis must be conducted, the general recommendation is annually. However, risk analysis should be revisited whenever significant changes occur within the organization, such as adopting new technology, expanding the workforce, or altering business operations. If a change to how and where PHI enters, lives within, or departs your practice occurs, potential threats to the security of that PHI must be evaluated. Periodic assessments help ensure that Policies and Procedures remain effective in protecting client data and contain the requisite safeguards.
Security Measures Degrade Over Time
The OCR underscored the idea that security measures tend to degrade over time. Threats and attacks evolve, and workforce may become complacent or forgetful about security protocols and adherence to Policies and Procedures. This highlights the importance of ongoing security training and awareness to maintain a culture of PHI protection.
Risk analysis is essential for assessing threats and whether security measures in place are sufficient for addressing current and reasonably anticipated threats. Without a risk analysis process the identification of degraded and insufficient measures typically occurs when those degraded measures fail and a security or breach incident occurs. Risk analysis is a way to proactively address the security of client info, and is far preferable to being in a position of reactively navigating breach investigation, documentation, and reporting.
Scalability of HIPAA
The OCR emphasized that what meeting the requirement for a thorough and accurate risk analysis entails can and will vary based on the size and complexity of the organization. What it looks like for a hospital versus a group practice versus a solo practice will differ. Smaller entities, such as mental health practices, should not be overwhelmed by the task. The OCR acknowledged the different scopes of risk analysis, but insists on its fundamental necessity as it is imperative for all HIPAA covered entities.
The OCR’s emphasis on the HIPAA Security Rule’s Risk Analysis requirement sheds light on the critical role of risk analysis in safeguarding client data in mental health practices. Risk analysis is not just a regulatory burden but a valuable tool for protecting sensitive information and ensuring ethical care. Mental health professionals must recognize its importance, conduct regular assessments, and stay vigilant in the ever-evolving landscape of data security. Compliance is a process, not a one-time task, and it is integral to providing the best care possible to clients.

