 If you love your smartphone as much as I do, you probably end up having confidential client info (read “protected health information” or “PHI” in HIPAA lingo) on it. This could be as simple as client names and numbers in your contact book and calendar (like I have) or as complex as clinical exchanges via text and email or even apps used to access your online health record system.
If you love your smartphone as much as I do, you probably end up having confidential client info (read “protected health information” or “PHI” in HIPAA lingo) on it. This could be as simple as client names and numbers in your contact book and calendar (like I have) or as complex as clinical exchanges via text and email or even apps used to access your online health record system.
Apple has a huge share of the general consumer market and has been pushing iPads into the medical market for years. Many attendees at my seminars are carrying iPhones and ask about how to keep client info safe when using these handy devices.
With iDevices (iPhones and iPads), there is no way to achieve a security setup that can earn you safe harbor from the HIPAA Breach Notification Rule (see this article for more info) Instead, the security approach is a strategic increase in vigilance around protecting the device and the info on it. Fortunately, Apple provides a number of ways to help us do this (remember what I said about how they really want iPads in the medical market?)
As this is a detailed article about securing devices for use in health care, I wish to stress at this time that this article is for educational purposes and is not legal advice. You should consult an attorney or qualified health IT security specialist if you’re looking for specific legal advice.
In a departure from their usual silence on HIPAA guidance issues around tech, the Department of Health and Human Services has published several videos and guidance pages on using mobile devices in clinical practice. You can read the list of recommended security features here: DHHS’ Site For Mobile Devices.
The guidance from DHHS is for mobile devices in general. Below are the specific points from the guidance that I want to address around iDevices. Note that in order to do the following things, you’ll need to make sure you know your Apple ID and password (you have to enter them when you download new apps from the App Store.)
Remote Tracking: did you know that you can go online and find your iPhone or iPad on a map just by entering your Apple ID and password? It’s true. And it is simultaneously awesome and creepy. So long as your phone/tablet is getting a cellular signal or is connected to WiFi, it can be located. This is essential for situations where your device gets lost. If you can retrieve it, you may not need to report a security breach, depending on what happened to it while it was lost. (BTW, you can also use this to find Macintosh laptops!)
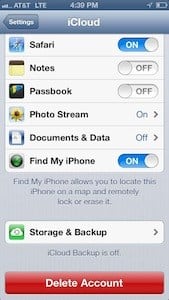 In order to use this feature (and the Remote Wipe feature), you need to make sure it is turned on. Here’s how: iCloud: Set up Find My iPhone
In order to use this feature (and the Remote Wipe feature), you need to make sure it is turned on. Here’s how: iCloud: Set up Find My iPhone
Here’s a good step-by-step description of how to use this feature: How to Use Find My iPhone to Locate Lost or Stolen iPhone
Remote Wipe: Were you unable to find your phone or tablet? Or did you locate it only to discover that you can’t get to it? Remote wipe is the last-ditch defense to try to avoid a security breach. When you activate a remote wipe, the Apple network will attempt to contact your device and tell it to delete everything. If successful, it will remove all the data from your device. Yes, all of it.
This feature depends on your device being connected to cellular towers or a WiFi network, so it’s not perfect. It’s also time-dependent. If you want to be able to argue that no security breach happened when you lost your device, you’ll need to either retrieve it quickly or wipe it quickly. So as soon as you discover your iPhone or iPad is missing, you’ll want to spring into action to either find it or wipe it.
Here’s a handy tip that will make it easier for you to decide to wipe your device when you discover it’s missing: whenever you sync your iDevice with a computer through iTunes, you can create a full backup of its data. iTunes will have a check box that lets you turn that feature on. If your device is wiped, you can use the backup from your computer to restore your data and apps to a new iDevice (or to the old one if you manage to find it.) One caveat, however: once you wipe the device, you can no longer use the Remote Tracking feature to find it! Wiping the device means saying goodbye to it.
If the device isn’t connected, you can still try to wipe it. The Apple network will send the “wipe signal” to the phone or tablet as soon as it comes online. I can imagine it being pretty nerve-wracking to wait around for a lost device to come back online — which may never happen — but it’s better than doing nothing.
Here are Apple’s official instructions for using Remote Wipe on iDevices: iCloud: Erase your device remotely.
Encryption: Apple’s marketing is a bit deceptive around this topic. iDevices are capable of excellent encryption, but they only use it for the Mail app. That means if you use the built-in Mail app, your emails and attachments are well-encrypted on the device. Note that this is not the same as using an encrypted email service, such as Hushmail. This just makes sure that the message and attachment files stored on your phone are kept secure while they sit there.
For whatever reason, Apple does not apply the encryption capabilities to your calendar items, contact book, text messages or any other apps that come built-in with the device. Other software developers can use the encryption capabilities in their own apps, however. So if you decide to seek out special apps to help you store files securely on your iDevice, their encryption can be strong and of high quality (so long as you use a strong passcode — see below.)
When you connect to a secured Web page or, perhaps, your cloud-based electronic health record system, iDevices can use the same strong, high-quality encryption for the Internet connection that your computer uses. This is important for when you wish to use sensitive online services from your iDevice.
Remember that you don’t have to encrypt all the data on your phone or tablet in order to be HIPAA-compliant, especially if you make use of the other security features like remote tracking, remote wipe, and good passcodes.
Even though the encryption is very limited, you should make sure you set it up properly. When your phone or tablet is turned on (which is probably all the time for your phone), the encryption’s strength entirely depends on your passcode’s strength. So…
Passcodes: Besides being a good way to keep nosy friends out of your phone, passcodes on iDevices are tied to the under-the-hood encryption system. The stronger the passcode, the stronger your encryption key becomes for protecting messages in your Mail app or other apps you download that use the encryption feature.
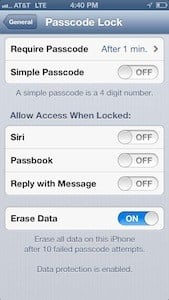 What’s more, Apple devices have a handy feature called Data Protection. When you activate Data Protection, and set the “Erase Data” feature to “On,” then your phone will erase itself if anyone enters the wrong passcode 10 times. This is a powerful tool for preventing security breaches. Most lost phones and tablets are grabbed or picked up for their inherent value and not because someone wants to see your contact book. Most people can’t guess a passcode in less than 10 tries, so the “Erase Data” feature gives you an increased level of confidence that someone who picks up your phone or tablet can’t necessarily get to your confidential data — at least not quickly. Here are Apple’s instructions for activating Data Protection and the Erase Data feature: iOS: Understanding data protection.
What’s more, Apple devices have a handy feature called Data Protection. When you activate Data Protection, and set the “Erase Data” feature to “On,” then your phone will erase itself if anyone enters the wrong passcode 10 times. This is a powerful tool for preventing security breaches. Most lost phones and tablets are grabbed or picked up for their inherent value and not because someone wants to see your contact book. Most people can’t guess a passcode in less than 10 tries, so the “Erase Data” feature gives you an increased level of confidence that someone who picks up your phone or tablet can’t necessarily get to your confidential data — at least not quickly. Here are Apple’s instructions for activating Data Protection and the Erase Data feature: iOS: Understanding data protection.
So how do you make sure your passcode is strong enough? By default, iDevices use 4-digit pin codes. These passcodes are quite weak. For clinicians who use these devices to store confidential info, it’s wise to enable longer passcodes. I recommend you use a passcode with at least 7 characters, but 10 characters would be great. Here’s a nice article on how to set up long passwords, along with some advice about preventing excessive passcode hassles: Secure your iPhone with strong yet easy to enter passcode.
Firewalls and Antivirus Software: There is no (legal) way to get a firewall or antivirus software on an iPhone or iPad. The architecture of these devices actually makes this quite a bit less of a concern than it might be on a computer or Android phone, however. This is a good reason to make sure you keep up with software updates for iOS, as Apple should be working to patch security holes as they become apparent.
Keep Siri Under Wraps
 A lot of people don’t like Siri, but I find it really useful. In fact, the voice-activated feature called Siri can be used to access a lot of stuff on your phone. What’s more is that you can use Siri even when you haven’t yet logged in to the phone. For that reason, you should disable the use of Siri when the phone is unlocked. Yes, this means you’ll have to enter your now-quite-long passcode every time you want to use Siri. Security costs are usually paid in inconvenience.
A lot of people don’t like Siri, but I find it really useful. In fact, the voice-activated feature called Siri can be used to access a lot of stuff on your phone. What’s more is that you can use Siri even when you haven’t yet logged in to the phone. For that reason, you should disable the use of Siri when the phone is unlocked. Yes, this means you’ll have to enter your now-quite-long passcode every time you want to use Siri. Security costs are usually paid in inconvenience.
To make sure Siri can’t be used without first entering the phone’s passcode, go to your Settings app, then tap on General, then tap on Passcode Lock. You’ll see Siri listed underneath “Allow Access When Locked.” Be sure to set it to “Off.” Don’t worry, you can still use Siri when you’ve unlocked your device.
About Auto-Login To Email and Other Apps
Many people set up their email app or other apps to automatically keep them logged in in so they don’t have to enter their password each time they open the app. This means that when you tap your Mail app or Gmail app it opens right up — no need to log in every time you tap it.
This is very handy, but it also reduces the overall security of any PHI that is stored on the Internet and can be accessed by the app. E.g. if you have any PHI in your Gmail account, and you have a Gmail app or you access your Gmail account through the Mail app, that PHI could be accessed by anyone who picks up your iDevice and can figure out your device’s passcode. Certainly if you use a strong passcode for the whole device, then you reduce the risk of security breaches that could result from your apps keeping you logged in.
One reason to make yourself enter your passwords every time is to reduce headaches if ever lose your device. If you lose it, and you want to avoid having to report the loss to your clients and the federal government, you’ll need to be able to reasonably show that none of your PHI was improperly accessed from the lost device. This may be more difficult to do if you know that your Internet-stored PHI becomes accessible to anyone who can get past your device’s passcode.
It’s useful, here, to think about how banks manage their online banking apps. I’ve used two different online banking apps before, and both of them require me to enter my username and password every time I access the app. Other security-minded apps, such as the mHealthText and qliqConnect secure texting apps, have similar schemes for logging in. Treating your other apps that access online PHI in the same manner would certainly reduce your overall risks of a confidentiality breach.
Documentation
What we described above would be called in HIPAA terms, “Technical Safeguards.” For actual compliance, you would need to also implement “Administrative” and “Physical Safeguards.”
Essentially, you’ll need to devise policies around who accesses your iDevices and how, how they are kept safe, and what your procedure is for when a breach is discovered (e.g. when you find it’s missing or you have reason to think that some unauthorized person accessed the phone or tablet.)
The process of properly documenting for HIPAA compliance might take some study, but is ultimately a good idea.
How can I learn more about security and confidentiality with mobile devices?
The topics in this article are covered in our online CE courses: Digital Ethics, Security & Privacy in Psychotherapy Practice Management (4 CE hrs, $39) at the Zur Institute; and HIPAA Security and Privacy in Psychotherapy, Counseling and Mental Health Practices (10 CE hrs, $99), also at the Zur Institute.
Special thanks to Michael Swiernik, MD, for his consultation on understanding how iDevices use encryption in actual practice.

Roy, you are a real gift to the mental health profession. You understand both the tech and the mental health world – a rare combination. Thank you SO much for your well written, concise and rich content in your articles.
Connie Konikoff, Msw, Lcsw in Lafayette, La.
Thanks, Connie. I appreciate it! :)
Hi Roy,
Could you write another article dedicated to Siri? Apple saves and stores the speech input into Siri for 2 years, and may use it to improve their voice recognition service. Is it impossible for Siri to be HIPAA compliant because this is how they treat the data?
Hi Lucy,
Thanks for your question. You have a good point.
Remember that products and services are not HIPAA compliant or non-compliant, only covered entities (and business associates) are. This is important because it shifts the focus from “can Siri be HIPAA compliant?” to “can I use Siri and be HIPAA compliant?” The answer to the first is probably “no” and the answer to the second is definitely “yes.” I imagine the biggest risk with Siri comes in using it to voice dictate text messages and emails to clients, or to voice dictate into other apps that one uses to store protected health information. The solution is to not use Siri to dictate protected health information. Just make sure you type it.
Hi Roy,
Thanks for the article- great advice. In the case that you have a non-smart (no text enabled) mobile phone (and have to use a password to get your messages)…is this HIPAA compliant?
Hi Emily: Specific methods of security (e.g. putting a password on the phone) are neither compliant nor non-compliant. Compliance is a process of identifying risks and making a plan to reduce them. I recommend checking out our Therapy Tech show (free, it’s on YouTube) about HIPAA compliance for more details: http://www.youtube.com/watch?v=JllYcEeBZtw
For classic flip phones and candy bar phones, a passcode is about the only real security measure I know of. So it would certainly be a useful one to put in place.
Thanks for the advice Roy. I’ll check out the Tech show!
Hi Roy:
I read this article a number of months ago and found it very helpful. However, recently, a colleague brought this link to my attention (http://support.apple.com/kb/ht4865) which appears to suggest that Apple has upgraded its security. I was wondering if you could comment on whether these are changes that would meet the criteria for safe harbor. I was also wondering if Apple’s comment about encrypted keys suggests that a C.E. could use iCloud (i.e., Contacts and Calendar) for PHI and not need a BAA from Apple.
thanks
Hi Nancy,
Yes, I haven’t had a chance to really research and write about the new security features in iOS7, but I know it’s a significant improvement. All I’ve done so far is advise people to upgrade their iPhones and iPads to iOS7 as soon as they can. It really is a big improvement, security-wise.
As for iCloud: the feds have made it clear that anyone who stores your PHI online is a Business Associate, no matter how the encryption keys are handled. So until Apple starts offering BAAs for us, there’s no HIPAA-compliant strategy for using iCloud to store PHI. This is unfortunate, because a risk analysis of iCloud would show us ways that we can probably store some PHI on it and keep risks at reasonable and appropriate levels. The Business Associate rule is too rigid for that approach, however.
Hi Roy,
Thank you very much. This is very helpful to our practice! Would you share your thoughts on: In order to be HIPAA compliant does a covered entity need to have a BAA agreement with the technology provider for texting (I guess that would be the phone company) if it is used for counseling? If the answer is no, can one be HIPAA complaint and use texting as a means of counseling if the provider and client both use encryption on their phone? Do you think texting for counseling may be an option, while being HIPAA complaint, in the future if a BAA is offered?
Thank you again.
Hi Ray,
Well, that’s a big issue to tackle in a blog post. :)
You can try posting in our LinkedIn group and see if it spurs discussion: https://www.linkedin.com/groups?home=&trk=anet_ug_hm&gid=4203297
You can also schedule a consultation with me if you have questions about applying texting, etc in your practice: https://dev-personcenteredtech.com/web-consulting-services-and-fees/consulting-for-mental-health-professionals/